 Source: Shutterstock
Source: Shutterstock
It's getting harder for regulated financial services organizations – especially smaller ones – to recruit, train and keep the very talented and hardworking people who are responsible for the security and safety of your digital infrastructure. Demand for these people is at an all-time high, and the supply of well-qualified people who are willing to work at smaller organizations is low.
After three decades in cybersecurity, I've witnessed a shift in how cybersecurity teams work. They've moved from being the "Department of No" to the "Department of Keeping Us Safe While We Do Amazing Things." Your security staff are team players and are dedicated to figuring out how to keep the organization moving forward quickly and safely in the face of attackers.
Recommended For You
But right now is an especially bad time to be in the vulnerability management team at a credit union. Hackers really, really want to prey on financial institutions because their assets are fungible. Stories about cybersecurity breaches are everywhere, so it's easy to imagine what cybersecurity teams are up against.
With the rise of bug bounties, cybercrime-as-a-service and an ever-increasing reliance on all things connected, it's harder than ever to play defense. Published vulnerabilities and increasing attacks are outstripping your teams' ability to keep up, and they simply feel like they can't win. One of the leading reasons for this is that the tools they are using, which kept us safe in previous decades, can't keep us safe now. Let's take a quick look at why this is.
The History of Cybersecurity Technology
- Real progress was made in vulnerability scanning 15 years ago. Suddenly, we could know where problems were and fix them. Then, two things happened: The numbers of things that could be "wrong" went up by orders of magnitude, and the vulnerability scanner market became commoditized. While problems increased, innovation slowed and then stopped. Today, scanners create reams of data for where a problem "might be," and they spend most of their time arguing about who has the best reporting.
- Network probes showed theoretical pathways through our networks, revealing which paths could lead to critical assets. This was a step in the right direction, but even with perfect knowledge of your network access control lists, it's impossible to have a good defense without knowing what's happening on the endpoint and with your users.
- Threat feeds emerged. "Research-as-a-service" gave a better understanding of attacks happening somewhere else. But, like a home security system that indicates when burglars are in your town but doesn't know if your doors are locked or your safe is open, threat feeds predict abstract risk but can never confirm where real risk is on your network.
Fast Forward to Today
Teams that are responsible for the safety of an organization need your support to develop a modern vulnerability management program built on understanding risk using automation. Organizations that don't support this run the risk of staff turnover, unmanaged cybersecurity risk and a host of compliance issues. Even the people who stay will ultimately feel demoralized and exhausted.
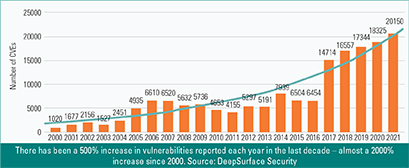 There has been a 500% increase in vulnerabilities reported each year in the last decade – almost a 2000% increase since 2000. Source: DeepSurface Security
There has been a 500% increase in vulnerabilities reported each year in the last decade – almost a 2000% increase since 2000. Source: DeepSurface Security Here are four practical things credit unions can do to better support their cybersecurity teams:
1. Stop counting network vulnerabilities. For two decades you've probably counted how many vulnerabilities surface and how fast you patch them. It doesn't work. Stop the focus on counting how many vulnerabilities you have, how many are patched, and how fast they were patched. This has been shown to incentivize activities that don't correlate with efficient risk reduction.
Consider that every network has a strong power law distribution where 90% of the risk is in 10% of the "critical" vulnerabilities that exist on that network. In a theoretical organization with 10,000 vulnerabilities that counts how many vulnerabilities it patches, it's possible to close 9,000 that contribute almost no risk to an organization while leaving the 1,000 that contain almost all of the risk and still have great metrics. Move from counting vulnerabilities to measuring risk.
2. Stop fixating on critical assets. While it's important to patch the critical systems, realize that nobody steals an organization's crown jewels by exploiting a critical vulnerability on the host that houses that data. These hosts and the networks they are on are well inside a network and protected by layers of defenses.
Of course, these critical assets may be compromised, but if they are, it's likely not due to being attacked. Much more likely it will be due to a patient attacker who slowly and carefully takes apart the organization's defenses piece by piece. They gather "escalations of privilege," moving from low-privilege to high-privilege, and then simply pivot to the sensitive asset with credentials. By the time they reach the asset they already have the keys to the kingdom. They won't break into your critical asset, they'll log in.
3. Measure objective risk to your organization. Next, incentivize the cybersecurity team to find, measure and reduce provable risk. They need to decide how to measure risk, but it's not rocket science. Let's look at some examples of relative risk measurement:
- If an attacker can combine two or three medium-level vulnerabilities and get to your crown jewels, that's an incredibly risky pathway.
- The shorter the pathway to an asset, the easier it is to exploit and the higher the risk.
- Say there is a pathway with one important step that requires user activity to be a successful attack. This can be clicking on a link or running malware. If your team can show that it's impossible to perform that activity on that host, then the risk is infinitely small for that pathway to be exploited. A vulnerability scanner, threat feed and network probe simply can't indicate if that user activity is possible on that box.
By allowing a cybersecurity team to calculate actual risk contribution of a vulnerability in the pathway instead of just its existence, it can better understand where real risk lies on your network.
4. Budget for, find and buy high-leverage power tools. It's critical to equip vulnerability management teams with power tools that simplify and streamline work they have to do. This work includes checking every host where a vulnerability exists and determining if the conditions are met on that machine to exploit the vulnerability. Remember that conditions can change daily on each host. This means that they need to automate.
Provide tools that walk the pathways and calculate the risk of chaining vulnerabilities together. Remember, that's how attackers think. They defeat in detail by taking one innocuous vulnerability and combining it with another until, quite suddenly, credit unions need help to figure out how it all went so wrong.
A Collaborative Effort
Help your team help you to solve your HR, risk and compliance issues. The tools that got us here won't get us there. Give permission to measure risk, not tickets. Invest in automation to check conditions on each host every day, and tools that can calculate the risk of chaining vulnerabilities together – this is how attackers think, and you must let your defenders work the same way.
Give them the right support and the right tools, and they will love their jobs and be empowered to find, measure and remove your organization's risk. Then, you'll solve most of your HR, risk and compliance issues surrounding cybersecurity.
 James Dirksen
James Dirksen James Dirksen Co-founder and CEO DeepSurface Security Portland, Ore.
Contact: [email protected]
© Touchpoint Markets, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more inforrmation visit Asset & Logo Licensing.






