 Employees with company financial access are the most targeted by scammers.
Employees with company financial access are the most targeted by scammers.
While ransomware like WannaCry draws the headlines, phishing is the cybercrime deceiving organizations consistently. Unsurprisingly those with access to company bank accounts, accounting and finance team members, are most frequently targeted.
The reality, 41% of organizations experience phishing attacks daily or more, and 77% experience a phishing attack at least once a month, according to a phishing report from UK-based security software firm Sophos.
Recommended For You
The study also revealed cybercriminals are adept at using social engineering to exploit human weaknesses. That is why everyone is on the front line when it comes to security. Beside the teams connected to company finances, cybercriminals also likely to target those who manage business processes and IT controls, which puts organizations at risk for ransomware and extortion. But cybercriminals do not discriminate. No role is safe from phishing. Anyone who receives emails is at risk.
John Shier, senior security expert at Sophos, said, "As the quality of phishing emails has improved it is important to remember that some recipients will get fooled. Users are the first line of defense against a successful phishing attack. While education is an important part of keeping an organization secure, so is the user's ability to report suspected phishing attempts." He added organizations should make it easy and blameless for users, even those fooled, to report attacks. "This early warning system is crucial for any organization wishing to respond quickly and decisively to a phishing attack."
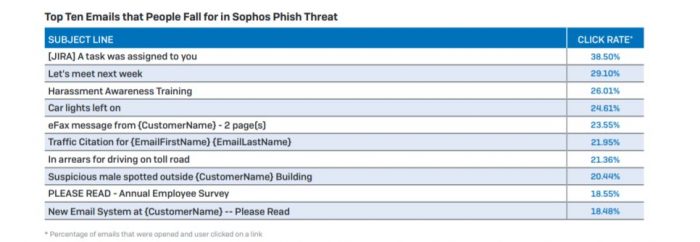 Image courtesy of Sophos.
Image courtesy of Sophos. The report's findings reveal interesting insights not just of the cybercriminals but of typical employees. Hackers are profiting off what gets peoples' attention, what they worry about, and what they are most likely to act on.
Results from Sophos Phish Threat, a simulation and training tool that teaches people how to spot phishing emails, show that individuals are most likely to fall for phishing emails that focus on:
- Simple, task-based activities referencing known applications: For example, "[JIRA] A task was assigned to you," which produced a 38.5% click rate.
- Mundane day-to-day topics: For example, "Let's meet next week" or "Car lights left on."— 29.1% click rate.
- Implication of wrong-doing: For example, "Harassment Awareness Training"—26.01% click rate.
- Car lights left on—24.61%.
- eFax message from {CustomerName} – 2 page(s)—23.55%
- Traffic Citation for {EmailFirstName} {EmailLastName}—21.95%
- In arrears for driving on toll road—21.36%
- Suspicious male spotted outside {CustomerName} Building—20.44%
- PLEASE READ – Annual Employee Survey—18.55%
- New Email System at {CustomerName} — Please Read—18.48%
The report results revealed a critical point for all organizations: "While we're getting wise to fancy visuals and too good to be true offers, peoples' defenses are down when it comes to everyday work-related emails. Clearly, lack of excitement in an email does not equate to lack of risk.
The important take-away here is that everyone needs to be on our guard all the time, and even the most mundane looking emails can hide a nasty sting, the research report explained. "While phishing often feels like an endless game of cat and mouse between cybercriminals and IT pros, with each side fighting to get ahead of the other."
The report noted there is no silver bullet when it comes to phishing, but Sophos recommended a three-pronged approach to ensure strong anti-phishing defenses. 1. User education and training. 2. Pre-delivery: Email gateway. 3. Post-delivery: Next-gen endpoint protection.
"Regular phishing training and education for all staff, using frequently refreshed resources, is the best way to secure your front line against phishing. End users can be any organization's greatest threat vector, but well-trained staff can improve your cybersecurity across the board," the report recommended.
The security firm said the Sophos Phish Threat lets organizations educate and test users through automated attack simulations, quality security awareness training, and actionable reporting metrics. "On average, customers see a 31% reduction in phishing susceptibility after just four Phish Threat trainings."
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.






