The Target breach is just the beginning, experts told Credit Union Times. Thieves will continue to find ways to access valuable financial and personal data.
Here are three reasons why:
1. Because they can.
By far, the main reason thieves have begun to steal card data from U.S. firms, some experts say, is because they can.
“The U.S. payments industry has become the one household in the neighborhood that has not upgraded its security system while everyone else has,” explained Karisse Hendrick, program manager in payments and fraud for the Merchant Risk Council, an international trade group that is organized to help firms fight card fraud. “When you are perceived to have security that is the easiest to beat, she added, thieves will try to beat your security.”
Breaches have their roots in the three large shifts in the global payments, technology and U.S. economic and political environments. Hendrick pointed out that the payments industry in the U.S. is perceived as among the richest, further heightening its desirability as a target.
“Those two things combine to make U.S. firms the biggest targets for data security breaches and subsequent fraud,” Hendrick said.
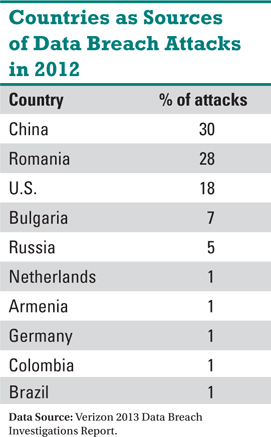
Further, the U.S. has not become the leading data theft target overnight in the country, Hendrick noted. International criminal interest in the U.S. has been growing for years, as Verizon documented in its 2013 Data Breach Investigations Report.
As other countries have gradually tightened their security systems and implemented tools such as smart-chip cards with the EMV standard, the U.S. fraud prevention protocols have fallen farther behind, the Verizon report said. It's not that the Payment Card Industry Data Standards have not done a good job, the technology they were protecting is simply not as secure as other payment's technology, Hendrick explained.
Read more: Thieves have upgraded their programming skills …
2. Thieves have upgraded their programming skills.
The second reason data breaches are here to stay is because thieves have gotten better at writing programs to steal the card data, industry watchers have found.
For instance, even though the phenomenon of a malware package that infected POS terminals came to widespread attention with the Target breach, the FBI has reported there were at least 20 breaches that used a similar approach. Further, the agency said it appeared thieves had used at least one malware package to test out firm's defenses. When that package they were developing had not performed well enough, the thieves created another one that worked better from their point of view.
3. Card issuers and retailers lack unification.
The third reason that breaches are likely to continue is the lack of a coordinated or unified approach to the challenge they represent. Previously, the U.S. payments industry was cohesive because card issuers and retailers agreed they better when consumers used a card to pay for goods and services as opposed to cash.
Retailers benefited from not having the risk of theft that came with cash and from the quick and guaranteed payments that cards represented over checks. Card issuers also gained from the interchange that card transactions generated by not having to pay for check processing. But the unified front has largely broken down in the face of retailers' legal and legislative challenges to interchange and the resulting controversy has undermined the payments industry's ability to work together to confront the problem.
Executives with the National Retail Federation, one of the organizations that supported the Durbin Amendment's cap on debit interchange for issuers with more than $10 billion in assets and sued the Federal Reserve to lower them, complained that the current approach to card data security does not work and is costly to retailers.
Doug Kantor, a partner with the Washington-based law firm of Steptoe and Johnson, helped represent the NAR in its legal fight with the Federal Reserve and laid out some of the trade group's complaints about the current card data security regime in an interview with Credit Union Times.
Kantor said retailers already pay nearly all the costs of card data security on the acquirer side by making sure their systems comply with industry security standards. However, those retailers currently have no say in setting those standards.
“The data security standards come entirely from the card brands and card issuers without any input from retailers,” Kantor said. “Also, the data security standards don't provide full proof protection from breaches and, if there is a breach, the retailers face enormous expenses in fines from the card brands and possible legal action.”
He said retailers believe the new chip cards on the EMV standard provide a very promising means of combating the threat but retailers want to play an active part in the new technology.
To illustrate, the card brands are currently adopting a standard for EMV cards that will not always require a PIN. These cards will have a magnetic stripe that will allow them to be swiped and a chip to provide data in real time which authenticates the transaction and the card.
Retailers believe this leaves them open to greater fraud risk and want the U.S. to mandate the use of PINs, Kantor said. Visa and the other card brands argue that in an economic environment like the U.S., where almost all transaction are going to be online and thus verifiable in real time, the PINs are not needed.
Read more: What can credit unions do?
Assuming the two different parts of the payments industry remain divided and criminals continue to develop novel attacks on payment systems, how can such efforts be countered and fraud losses limited?
First, some experts agree it is never too late to re-emphasize basic computer security and procedures. At press time, retailer Target acknowledged that the malware that infected its POS terminals was introduced by someone who stole the credentials of one of its vendors in order to gain access.
“This recent announcement from Target confirms that the biggest breaches are due to insider threats, especially with privileged users and administrative access,” said Eric Chiu, president & co-founder of HyTrust, a Mountain View, Calif.-based data security firm that focuses on the cloud. “The bad guys are now using advanced threats to steal credentials and pose as employees, and once on the network, they look the same as good guys.”
Chiu said access controls, role-based monitoring and data security are critical to securing against these new insider threats, especially in cloud environments that concentrate systems and data.
Second, credit unions should start to live with the assumption that their members' cards will likely be breached at some point and plan for those breaches.
Carlton Howard, vice president of risk management at the $2.2 billion Coastal Federal Credit Union in Raleigh, N.C., said daily checks, security blogs and data tracking sites are used to get an advance warning of any breaches so that there is enough time to craft a strategy.
Coastal also has a pre-purchased number of plastics on hand at its fulfillment partner so that should a breach occur, the credit union can quickly reissue cards, Howard said.
The $1.9 billion Summit Credit Union in Madison, Wis., makes sure its fulfillment partner keeps its plastics on hand and has added card security breaches to its crisis management plans, said Becky Gerothanas, senior vice president for operations.
“The goal is make sure that we think out what to do and who is responsible for what if we have one of these things happen on a large scale,” Gerothanas said, adding, “so we aren't trying to figure it out as it happens.”
Both Carlton and Gerothanas also stressed the importance of communicating fully and often with members to alert them about the breach and to ask their assistance in helping the credit union protect their cards against fraud losses.
© Touchpoint Markets, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more inforrmation visit Asset & Logo Licensing.






